By Adrian | March 3, 2019
Warning - Dragons ahead
The following post is for educational purposes only. I intend to show you what can happen if you get infected with a remote access tool (RAT) and just how easy it is to setup the Command and Control (C2) server.
Don’t attempt to analyse malware on a system that you aren’t prepared to destroy and certainly do not be attempting this sort of analysis on ANY system you are not authorised for!
This particular RAT isn’t too sophisticated in the scheme of things. You have been warned.
Setting up the environment
To setup a quick environment for this I have 2 Windows 10 Virtual machines that have been configured using packer and vagrant. They are able to connect to each other.
QuasarRat can be downloaded from GitHub here. This will be installed on our “Red” machine. Google chrome will prevent the file from being downloaded so you need to disable “safe browsing” before you start.
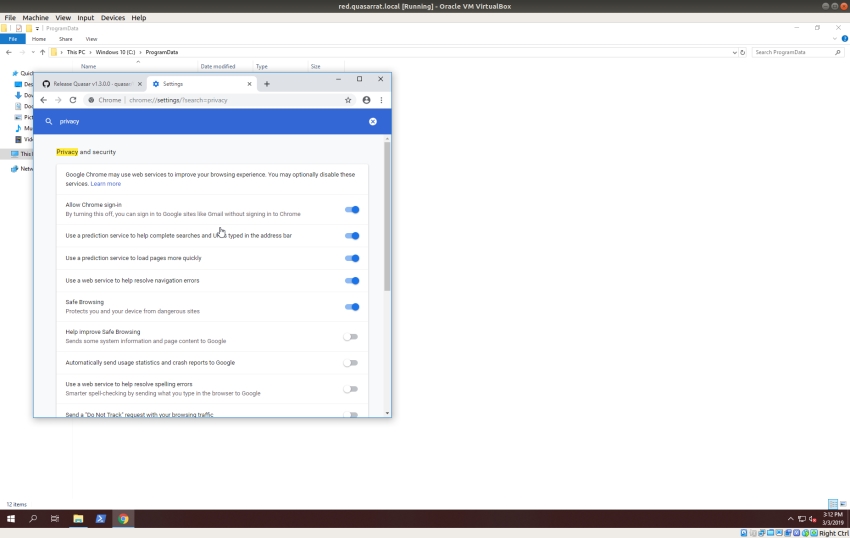
Disable safe browsing
Extract the zip file
QuasarRAT on first execution. Even the dodgy apps have a EULA
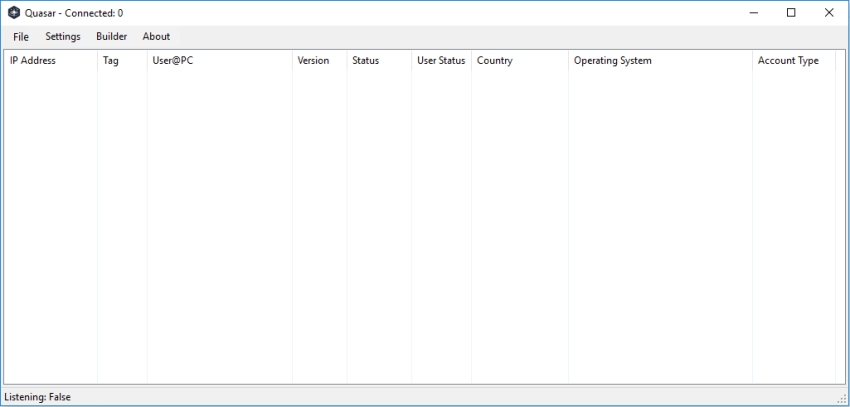
The QuasarRAT dashboard showing no connections
Setting up QuasarRAT Client/Server
In order to infect your victim you need to create a client to deploy. To create this select “Builder” from the menu. To generate a fairly plain client, add in your server IP and port (ive selected 443, as its nearly impossible to block it outbound)
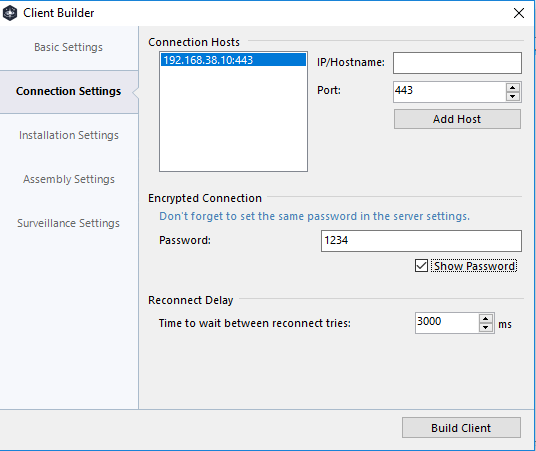
The installation settings is where you can get a little creative in how you name your client. Imagine for instance this was a “google updater” or an “iTunes Updater”. These 2 names alone might cause an unskilled end-user to ignore the executable.
We want to install this into the user AppData folder as we cant be sure that the local user has administrative access to being with.
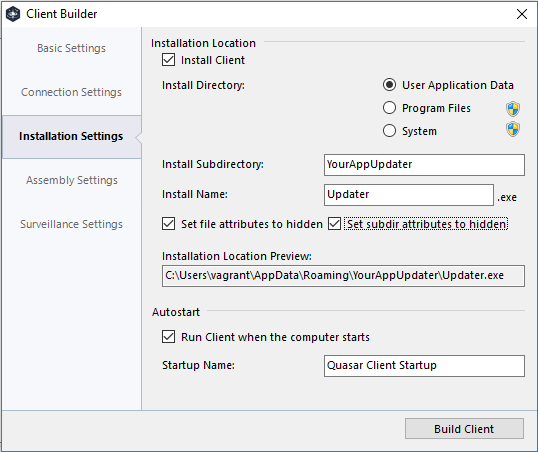
You can further obfuscate the file by updating its properties and assiging it an icon file. In this case ive used PowerShell
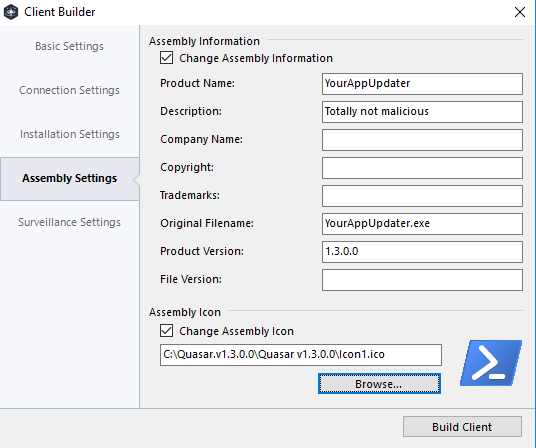
Finally enable the keylogger from the Surveillance page, this will give you an idea of what is possible from an attacker. You can even hide the folder, but in reality it could be easily discovered.
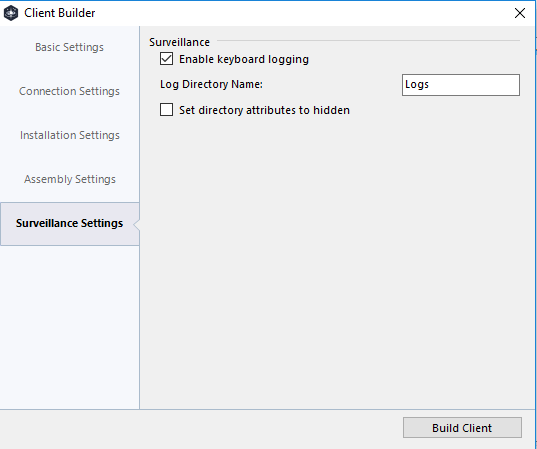
Now press “Build client” and wait about a minute.
Remember only install if you have permission
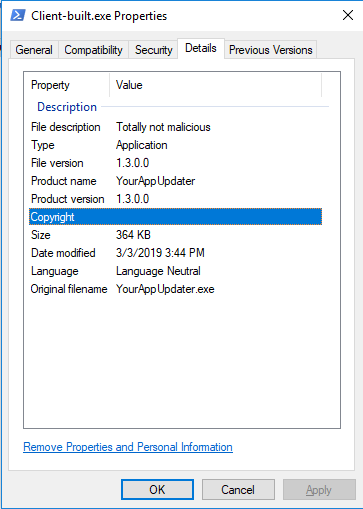
nothing to see here……
Now that you have generated the client, I want to show you that its quite noisy and seen for what it is… malicious. Now I could use a tool like VirusTotal for this but am using jotti instead.
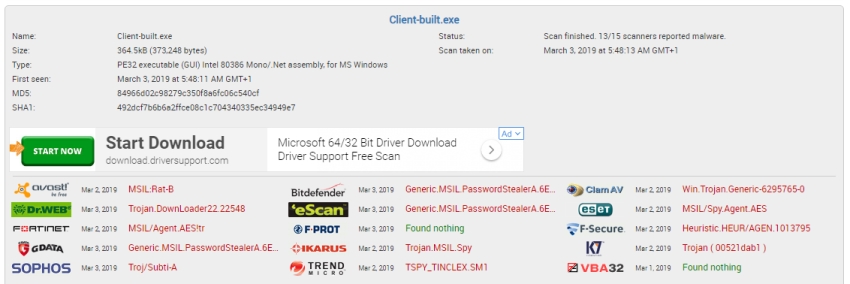
13⁄15 AV vendors see it as either a RAT, Password Stealer or spying agent. Totally malicious and should be blocked prior to installation by your Anti-Virus. Wheres the fun in that?
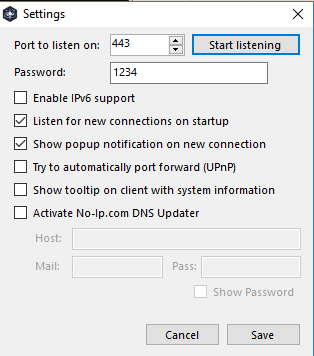
Back in the main Quasar console select “Settings” and have it listen on port 443.
Setting up the payload delivery
In terms of how to get the client to install this malicious application there are many ways that this is possbile. Using social engineering techniques you could:
- Have the user visit a website and download it
- Deliver the payload as part of an Office macro or malicious PDF
- Make it as part of an autorun from a USB
Or, if you are already connected to the network then why not just use PSExec to copy and execute it for you.

Victim connected
By this stage you should have your victim machine connected in. This is the scary part if your on the wrong end of this sort of tool.

Capabilities
Now that a machine has checked in we can perform the following.
Obtain System information
Lots of useful information here such as Operating System, uptime, CPU, GPU (want to mine some bitcoins?), also hidden from the screenshot is the ISP information.

File Transfer
Need to download or upload a file? you can very easily do this here.
Persistence mechanisms
Want to keep a foothold on that machine? well you can create that persistence.

Start/Stop Processes
Want to irritate the victim by killing their chrome processes or starting a calculator?

View network connections
Network connections can provide further intel about a victim. What websites they are visiting and through what processes. Oh hai there Google and Microsoft Singapore. You can also close off a network connection while you are at it.

View remote registry
Take a deep dive into the system and see what other applications are installed. Add/Remove your own keys.

Remote Desktop
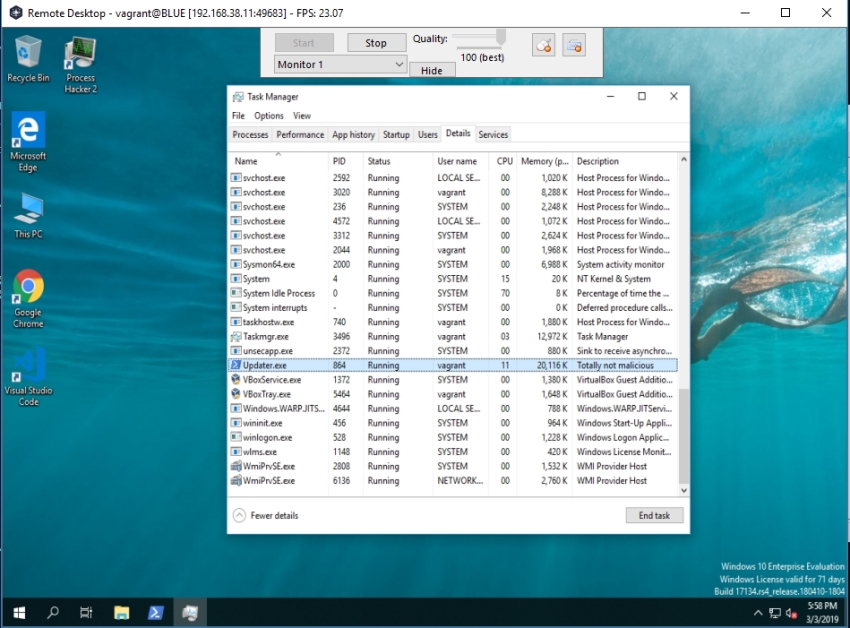
Now for some of the more malicious parts of this RAT. The remote desktop will allow the attacker to see whats happening on the desktop. They can even interact by using the keyboard and mouse. Couple this with the webcam and the attacker can really keep a close eye on things. The victim could close the updater.exe process here and the game would be up, unless you had set further persistence mechanisms.
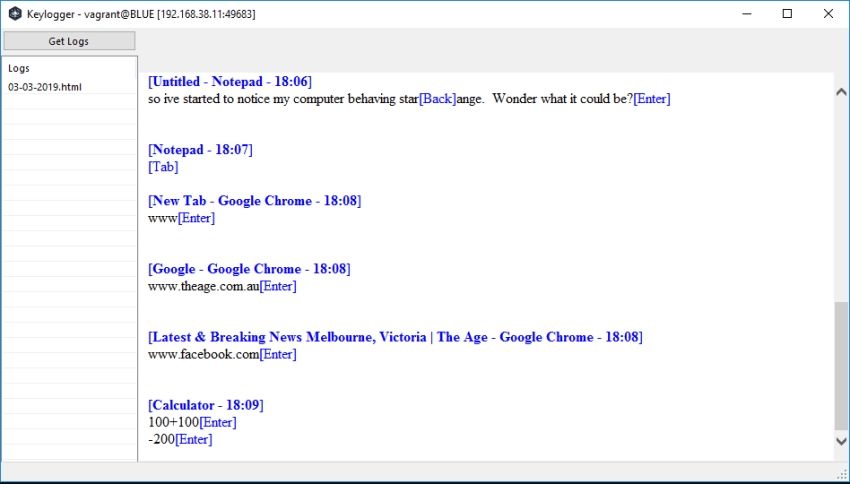
Keylogger
This is where RAT’s can get particually nasty. You think your entering in a password that being masked.. well they are in clear text here, along with all your other keystrokes.
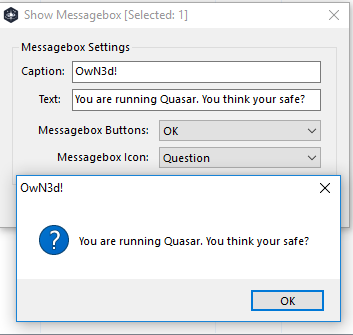
Send a message
Not sure what the purpose of this would actaully be.
Other Features
- Remote Standby / Shutdown and Restart
- Remote shell
- Password recovery
- Remote file execution
- Remote open a website
MITRE Attack Framework
According to the Mitre Attack framework there are multiple techniques in play here and avoiding delivery higher in the kill chain is ideal. This particular RAT should be caught by most if not all modern AV vendors. (I really had to weaken my security in order to get this to work!)
So there you go. This is what a real world RAT looks like. You just dont want to be on the wrong end of these things. If you do, get your machine rebuilt quickly and go about changing all your passwords. Remember to not share your password between websites and use a password manager wherever possible.


