By Adrian | April 22, 2020
OpenCTI is an open source Cyber Threat Intelligence platform that provides a powerful knowledge management database for storing, organising and sharing knowledge about cyber threats and uses the STIX2 schema for it structure. It has been designed for CTI analysts. The platform is built on Modern technologies of Grakn, GraphQL, Elastic, RabbitMQ, Redis and React. The project is available as a docker image which make installation simple.
While I’m probably not going to do the best job of talking up the full feature set of this platform, you can view more about it on their website and github page. Its well worth viewing the various presentations about this platform as well. One such presentation is here Building a Cyber Threat Intelligence Knowledge Management System Using Grakn
What I will say is that the development team behind OpenCTI have created a platform that is free, easy to use, visually appealing and gives CTI analysts a way to describe the various relationships between indicators and actors. The platform also has additional connectors to further enhance its abilities. For instance you can pull indicators from MISP into OpenCTI using the MISP connector.
For the installation of OpenCTI, I am using 2 x Ubuntu 18.04.4 virtual machines with 8Gb RAM and 20Gb disk assigned to each of them. They will need connectivity to each other and the internet, and can ping by hostname. Nothing else is special about them as such. Just a base OS that has been fully patched to begin with. I have named my machines opencti-1 and opencti-2. In hindsight, I probably should have named them as docker. Not a show stopper though as ill just be using them for OpenCTI and associated images.
Install Docker
Note: Both virtual machines will require Docker to be installed.
While you can install OpenCTI manually, save yourself the hassle and use the provided docker-compose file. To install Docker run the following commands. Steps taken from the Docker page.
Update the repositories
sudo apt-get update
Install prereqs
sudo apt-get install \
apt-transport-https \
ca-certificates \
curl \
gnupg-agent \
software-properties-common
Add the GPG Key
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo apt-key add -
Check the fingerprint of the key
sudo apt-key fingerprint 0EBFCD88
Add the stable repository
sudo add-apt-repository \
"deb [arch=amd64] https://download.docker.com/linux/ubuntu \
$(lsb_release -cs) \
stable"
Install Docker and Docker Compose
sudo apt-get update
sudo apt-get install docker-ce docker-ce-cli containerd.io docker-compose
Check installed version
sudo docker version
Manage docker as a non root user
Having to sudo every docker command is annoying so lets create a docker group and add your user into it. You will need to logoff and on again for the group to re-evaluate.
sudo usermod -aG docker $USER
Create Docker Swarm
While you don’t technically need Docker Swarm to install OpenCTI, this is how im going to be installing it as I want to incorporate more Docker containers for other features in the future.
From the first node (AKA: Manager node) run the following command:
docker swarm init --advertise-addr <MANAGER-IP>
The output displays a command on what you run on the other node to join this swarm. Run that command on the second node. It will join this node as a worker node.
docker swarm join --token <LONG-TOKEN-ID> <IP-ADDRESS-OF-MANAGER:PORT>
Install Portainer
While you might enjoy managing containers manually, and its probably something you want to get your hands dirty with, using Portainer will make your life much easier. The installation of Portainer is a matter of downloading a docker-compose file and deploying a stack. We will then use Portainer to add the OpenCTI stack.
This only needs to be performed on one node.
mkdir -p /opt/portainer && cd /opt/portainer
curl -L https://downloads.portainer.io/portainer-agent-stack.yml -o portainer-agent-stack.yml
Before you stand up Portainer, we need to change the client port as it will conflict with OpenCTI. You can make this change by editing the portainer-agent-stack.yml file. Locate the ports section and change them from port 8000 / 9000 to port 18000 / 19000 respectively. The configuration should look like this afterwards.
ports:
- "19000:9000"
- "18000:8000"
With the ports changed, we can now stand up Portainer using the following command:
docker stack deploy --compose-file=portainer-agent-stack.yml portainer
You can then login to Portainer by using the ip:19000 and setting your initial password
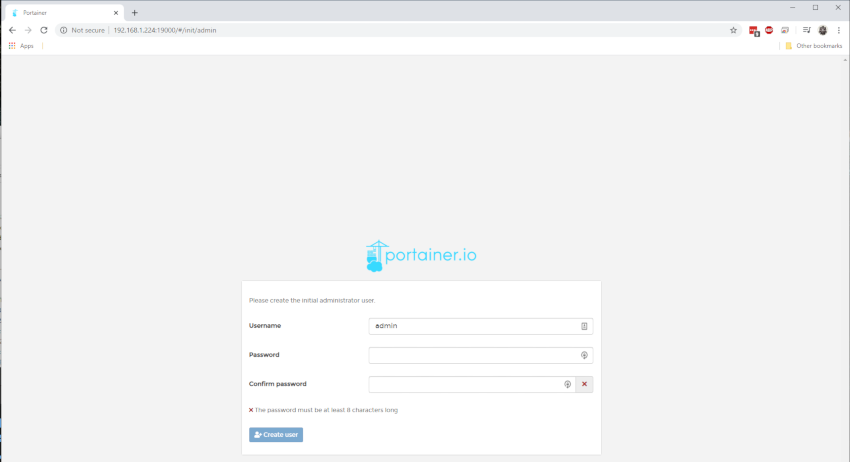
The GUI provides a comprehensive overview of your Docker stack environment.
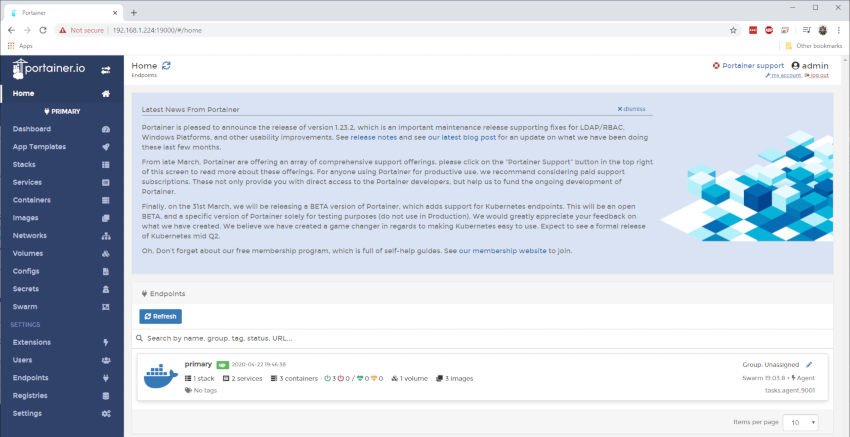
Install OpenCTI
Now we have Portainer installed, we can create the OpenCTI stack. This will be done within the Portainer interface.
The installation notes for OpenCTI on Docker can be found over at notion.io
I found the installation steps were quite general and contained some assumed knowledge. Some of the information was in another README file, and I chose to use Portainer, so these were the steps that I took.
Obtain docker-compose.yml
Download or copy the contents of https://github.com/OpenCTI-Platform/docker/blob/master/docker-compose.yml. While you could stand up your own git repository for this and point portainer at it, I am just going to keep this as a standalone system and I plan on making further changes to the docker-compose file in a later post.
Within Portainer, Select Stacks from the left hand pane, and Add stack. Give the stack a name, and use the web editor to paste in docker-compose.yml file that was downloaded.
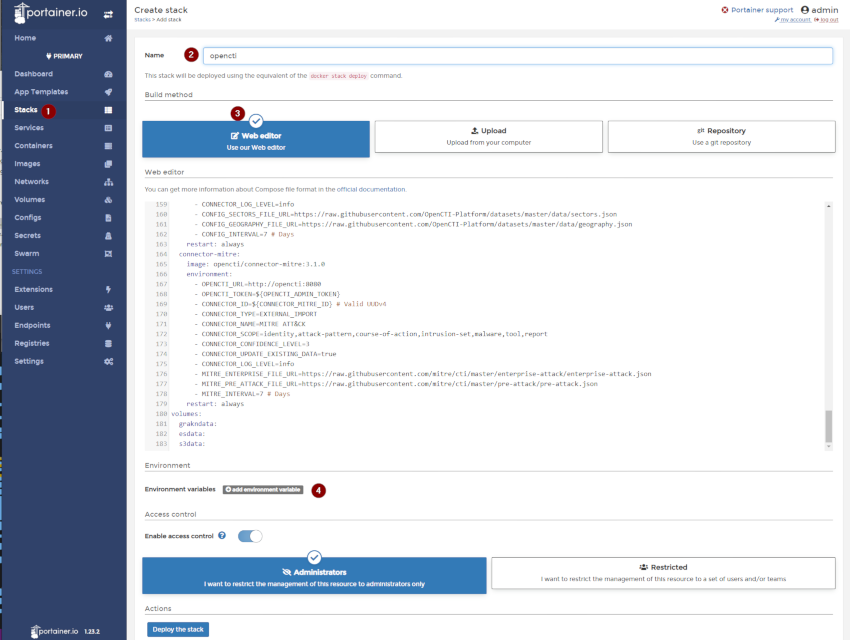
Before we deploy the stack we need to create a number of environment variables. If you look at the docker-compose.yml file, you will notice a heap of ${VARIABLE} entries. We can add these as Environment variables.
OpenCTI provides a sample .env file https://github.com/OpenCTI-Platform/docker/blob/master/.env.example which can be used and modified. Goes without saying that you should be creating your own strong passwords. Each line item needs to be manually added into the environment variables section. There are 13 variables in total.
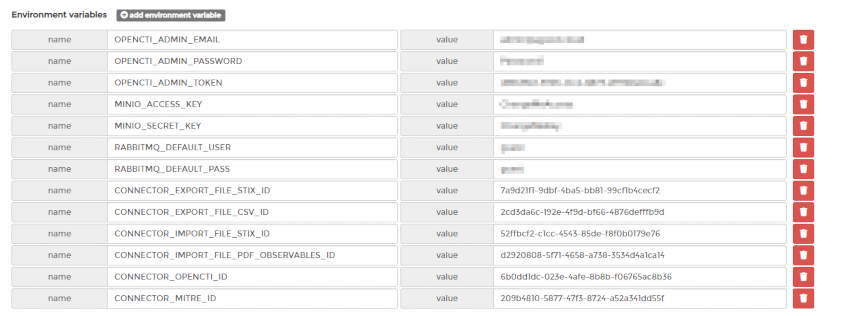
The environment variables are used so that credentials are not hard coded and stored within the docker-compose.yml file.
You will need to create a new UUID for the OPENCTI_ADMIN_TOKEN variable. A UUID can be generated using https://www.uuidgenerator.net/version4 or uuidgen from a linux command line.
Deploy the OpenCTI stack
With the docker-compose file added into the web editor and the environment variables filled, press the Deploy the stack button and wait.
From deploying the stack to OpenCTI being available took quite a while. Probably best to have a break while you wait for the stack to be ready.
All going well, you should be able to hit any IP of your docker swarm on port 8080 and get an OpenCTI logon page.

Once you login the OpenCTI dashboard looks like this:
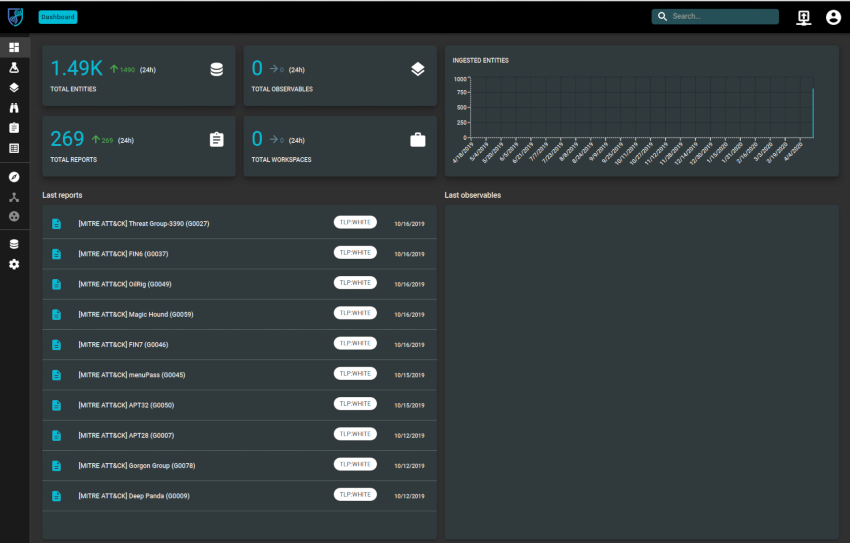
And thats pretty much it as far as the installation goes.
APT28
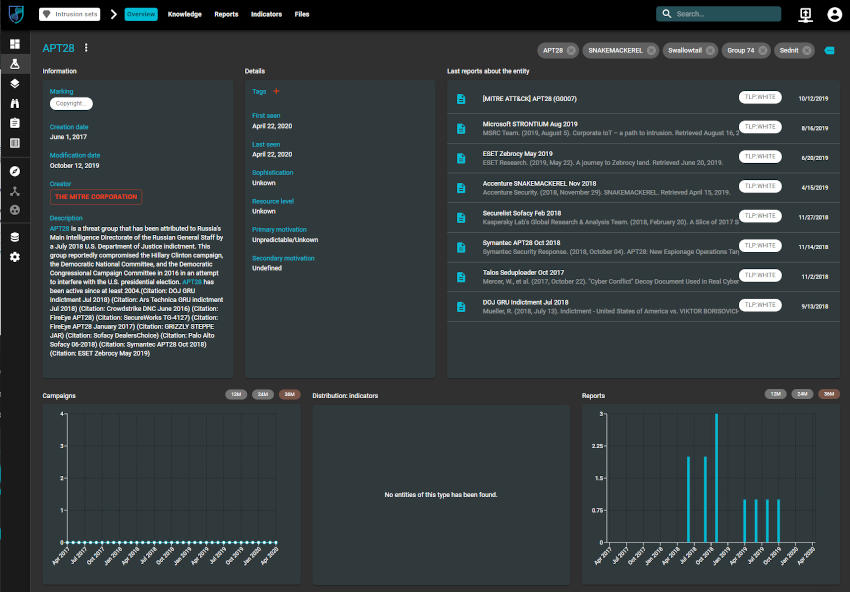
There is quite a bit of data that is provided out of the box. A good example of what OpenCTI’s is capable of is by checking out APT28.
Using the Flask icon (2nd icon on the left), navigate across to Intrusion sets and then select APT28. Here you can start to see details and reports.
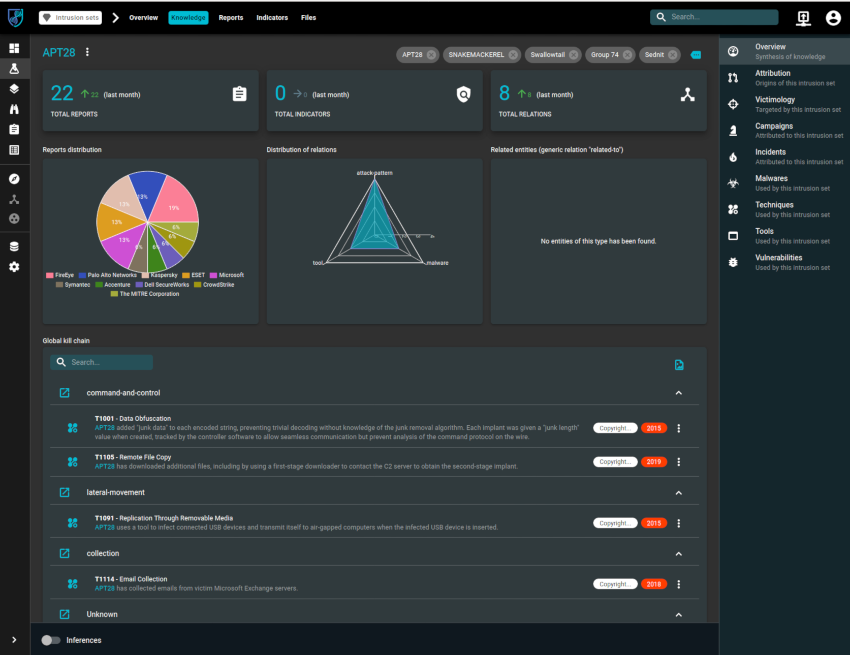
If you navigate over to Knowledge, you can start too see where the reports have come from, and the relationship between indicators and the TTP’s used by this group.
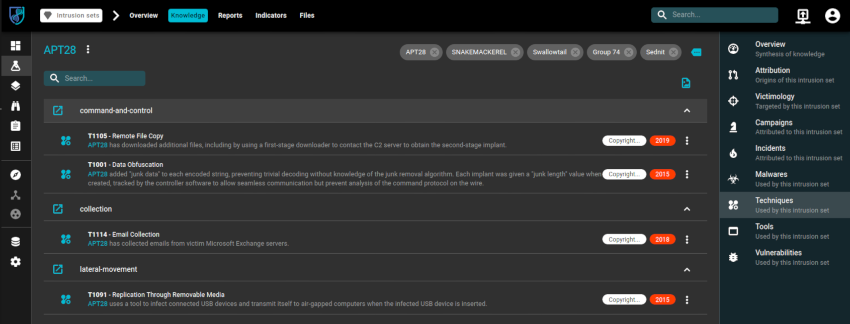
From the right hand pane you can see the various Malware, Techniques, Tools etc associated.
Conclusion
OpenCTI certainly looks like a very exciting and interesting platform to store and manage Cyber Threat Intelligence for your organisation. I hope to add in a reverse proxy docker solution and extend the functionality of OpenCTI using the various available connectors.

