By Adrian | September 24, 2019
This is part 5 of the Cortex build. In this part I’ll add, configure and test out an analysers. Links to the previous articles are here:
Part I - Building TheHive
Part II - Setup reverse proxy for TheHive
Part III - Building MISP
Part IV - Building Cortex
Part V - Adding analyzers to Cortex
Part VI - Setup reverse proxy for Cortex
Part VII - Integrate TheHive and Cortex
Part VIII - Integrate MISP to TheHive
Part IX - Upgrading TheHive
Part X - Updating MISP
Part XI - Upgrading Cortex
Part XII - Wrapup of TheHive, MISP, Cortex
Add analysers
Now that we have a base install completed, we need to add in the Cortex analysers. This is what allows you run an observable against various online intelligence systems such as VirusTotal, cymon.io, abuseipDB, urlscan and many many more. In fact, if it has an API and you know a bit of python you can write your own analysers and responsers. Cortex can also perform things like extracting headers from emails as well as pushing IOC’s out to other systems like Crowdstrike, ZScaler etc.
Install Cortex-Analyzers pre-reqs
sudo apt-get install -y --no-install-recommends python-pip python2.7-dev python3-pip python3-dev ssdeep libfuzzy-dev libfuzzy2 libimage-exiftool-perl libmagic1 build-essential git libssl-dev
sudo pip install -U pip setuptools && sudo pip3 install -U pip setuptools
Clone the git repository that contains all the analysers
cd /opt
sudo git clone https://github.com/TheHive-Project/Cortex-Analyzers
As each analyser comes with its own software requirements, we need to look at the requirements.txt file of each and install those components.
for I in $(find Cortex-Analyzers -name 'requirements.txt'); do sudo -H pip2 install -r $I; done && \
for I in $(find Cortex-Analyzers -name 'requirements.txt'); do sudo -H pip3 install -r $I || true; done
Then we update the Cortex configuration file and restart Cortex.
sudo nano /etc/cortex/conf/application.conf
# Modify the responder section
# path = ["path/to/Cortex-Analyzers/analyzers"]
path = ["/opt/Cortex-Analyzers/analyzers/"]
# Restart cortex
sudo service cortex restart
All the configurarion of the analysers in cortex is done within the GUI. This is where you will need to login with an orgadmin account and select Orginization, Analyzers for the new org you setup earlier.
Note: Responders cannot be configured on the default org.
Configure
As an example I have configured the VirusTotal_GetReport_3_0 and VirusTotal_Scan_3_0 analysers. For this particular analyser, you will need an account with http://virustotal.com and an API key. The free edition limits you to 4 requests a minute. This is suitable for low volume requests. The premium keys, well lets just say you need to request it and if you have to ask how much you probably can’t afford it. Online reports seem to indicate the cost starts at $10k a year.
Select Orginization, Analysers and then Enable on the Analyser you wish to configure. Add in the required settings for that analyser.
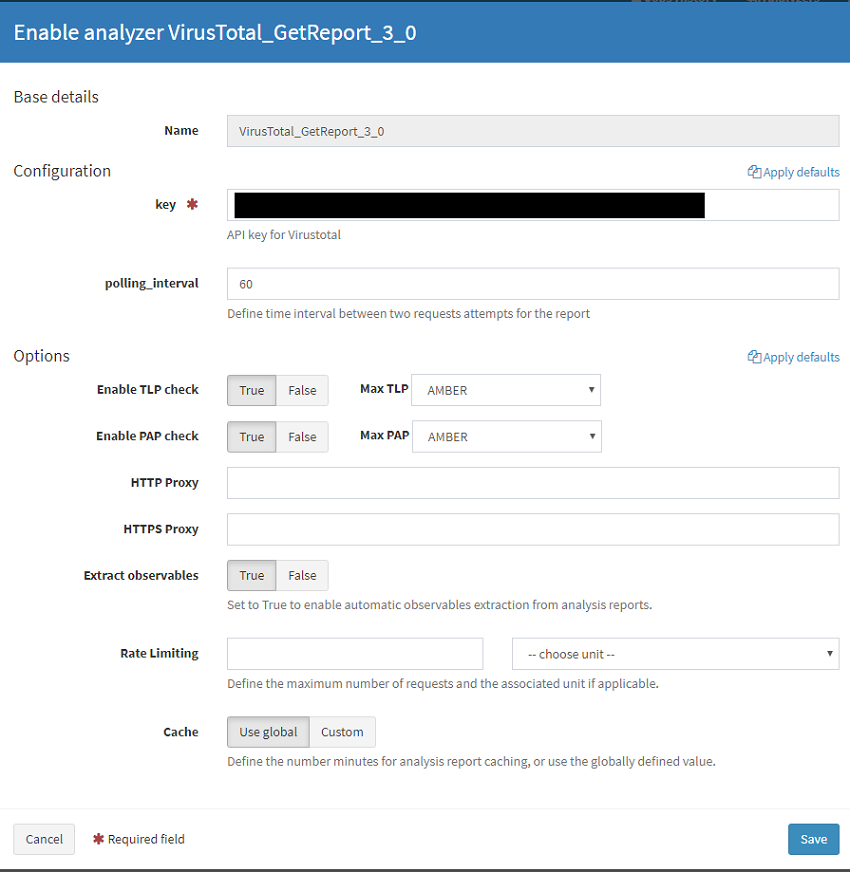
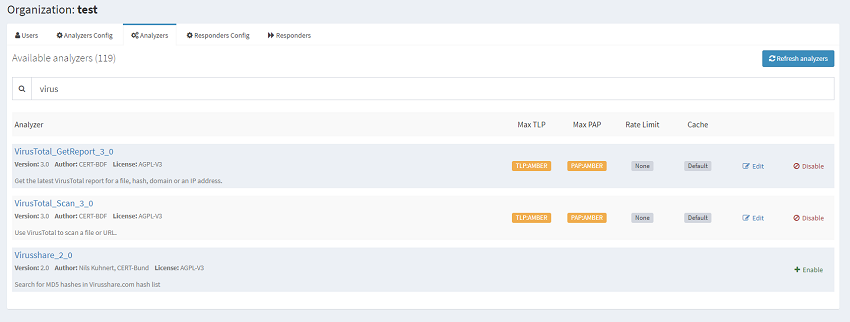
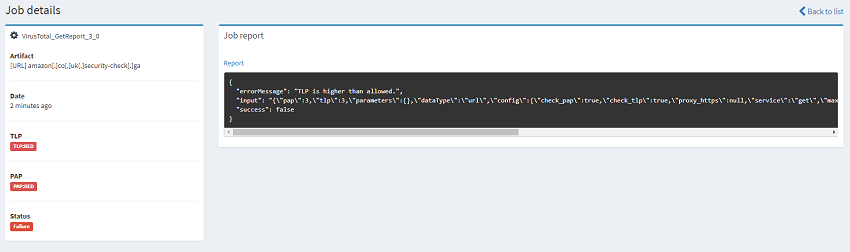
You can now use this analyser by selecting New Analysis on the top left part of the webpage. Here you can set the Traffic Light Protocol (TLP) and Permissible Actions Protocol (PAP) levels. When we configured the Analyser we set the TLP/PAP settings to AMBER so if we try to scan an IOC that is higher than this then the scan returns an error indicating this. For example if you have a file you are wanting to scan against VirusTotal and it contains potentially sensitive information, you may tag that as PAP/TLP red in which case attempting to run this analyser will fail saving a potential data breach.
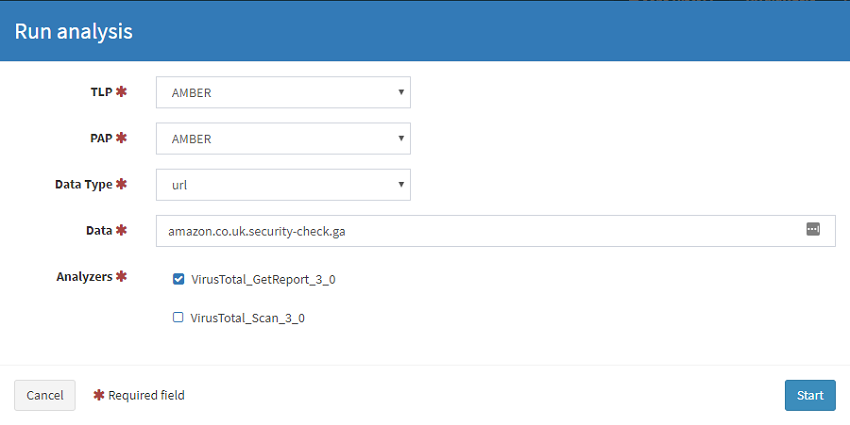 Running an AMBER IOC against the analyer configured with a MAX TLP as AMBER. Success!
Running an AMBER IOC against the analyer configured with a MAX TLP as AMBER. Success!
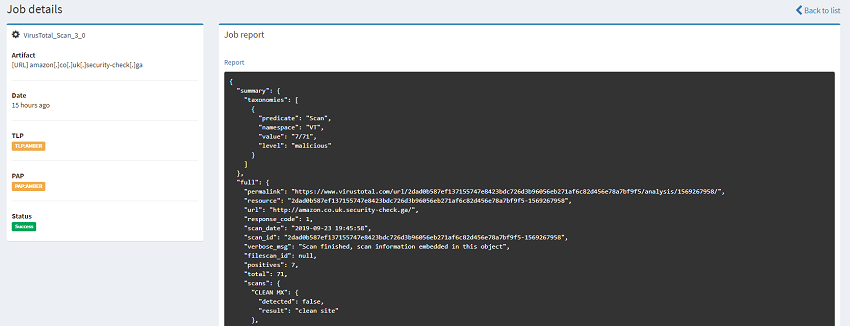 Running a RED IOC against the analyer configured with a MAX TLP as AMBER will throw an error which is exactly what your SOC may have prescribed.
Running a RED IOC against the analyer configured with a MAX TLP as AMBER will throw an error which is exactly what your SOC may have prescribed.
 In the next post ill go over adding a reverse proxy into the mix similar to what I did with TheHive.
In the next post ill go over adding a reverse proxy into the mix similar to what I did with TheHive.
References

