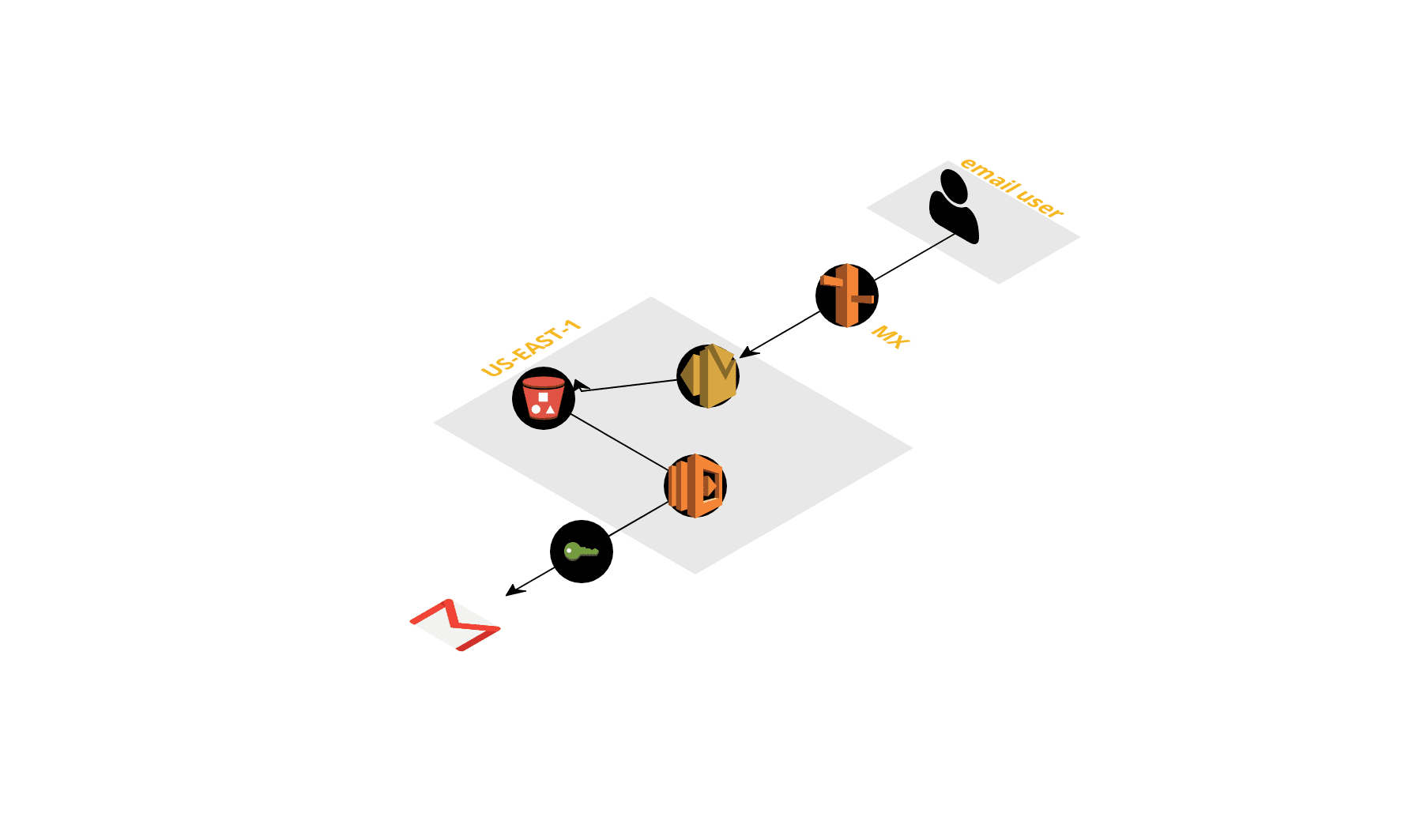
Fail2ban Setup
Fail2Ban is a great piece of software to keep those who would try (and fail) to access your services. It’s easy to setup as well, and can be as complicated as you want. Firstly perform the install by using this command. This will perform the install and create a service so that when you reboot, fail2ban will automatically start. sudo apt install fail2ban The configuration I am going to be performing will be for sshd, however there are stacks of pre-configured jails that can be used, and if it doesn’t have a pre-canned option, if your app has a log file file, then it can be customised accordingly.